"25.x.x.x" Registered To The Uk Ministry Of Defense?
The large news in the tech industry this calendar week is The Heartbleed Bug, a vulnerability that affects a large portion of secure web sites on the Internet. I updated the Wireshark and WinPcap web sites on Mon (along with reissuing and revoking certificates) shortly subsequently OS patches were released.
Our web sites are protected going forwards, but what near the past? We have a Shark appliance in our environment but that leads to a claiming. We had about 350 GB of HTTPS on our network on Monday alone. This is simply slightly also large to load into Wireshark.
Fortunately one of my coworkers (P.J. Malloy) came up with a BPF filter that matches Heartbleed traffic:
http://www.riverbed.com/blogs/Retroactively-detecting-a-prior-Heartbleed-exploitation-from-stored-packets-using-a-BPF-expression.html
Applying this filter straight on the Shark appliance gave me a much smaller number of packets which I could easily analyze in Wireshark. And so far I haven't found anything suspicious.
As nosotros all know, TCP/IP is a great protocol suite. However, at that place are times when it can go the bottleneck. This is peculiarly true if yous utilise TCP/IP for existent time transactions where small data sizes are the norm (remember financial institutions). In this session, I'll show you lot why Nagle algorithm and delayed acknowledgement was developed. But more importantly, I'll highlight the unintended consequences when the two features collaborate – desperately – with each other. After watching this session, you will be able to spot the hidden dangers of using TCP/IP for real time transactions. Enjoy, and every bit always, I would actually appreciate your feedback and suggestions. Here is the video:
And equally always, any and all feedback and proposition are welcome. Thank you and Enjoy!
Hansang Bae
Wednesday, August iv, 8:00 AM
We receive a phone call from someone complaining almost "Wireshark Antivirus". I have the call. The person on the other end isn't able to provide many details other than that a plan named "Wireshark Antivirus" is displaying some a shield and directing him to the cacetech.com web site.
This is new. We've been on the receiving end of a few imitation positives in the past but this is new. Some jackass is using our proper noun practise do harm.
This will non end well. Go on reading
I recently got an Android phone. Later on downloading the Android SDK I noticed that my cellular provider (T-Mobile) was doing something odd. Co-ordinate to the netcfg command they're using 25.0.0.0/8 on their GPRS/Edge network:
$ netcfg lo UP 127.0.0.ane 255.0.0.0 0x00000049 dummy0 Downward 0.0.0.0 0.0.0.0 0x00000082 rmnet0 UP 25.130.205.212 255.255.255.252 0x00001043 rmnet1 DOWN 0.0.0.0 0.0.0.0 0x00001002 rmnet2 Downward 0.0.0.0 0.0.0.0 0x00001002 sit0 DOWN 0.0.0.0 0.0.0.0 0x00000080 ip6tnl0 Down 0.0.0.0 0.0.0.0 0x00000080 T-Mobile doesn't own that netblock. The United kingdom Ministry of Defence does. Why would they exercise such a thing? After all, RFC 1918 gives you 3 whole blocks (10.0.0.0/eight, 172.16.0.0/12, and 192.168.0.0/16) to do with equally you please. Straying from those on your private will damn you to an eternity of network flakiness and give your twisted pair cabling scurvy, right?
Why this is clever
According to several BGP looking glasses and figure five of Geoff Huston'southward IPv4 Address Report the Ministry building of Defence doesn't advertise any routes for 25.0.0.0/8. That means that none of the 25.x.x.x addresses are existence used on the public Internet. If you're on a private network they're effectively gratuitous for the taking. But still, why aren't they using the officially-sanctioned RFC 1918 address?
My telephone also has an 802.11 interface. Let'south take a expect at netcfg'southward output when I'm connected to T-Mobile'south network and my domicile network:
$ netcfg lo Upwardly 127.0.0.1 255.0.0.0 0x00000049 dummy0 DOWN 0.0.0.0 0.0.0.0 0x00000082 rmnet0 Down 25.130.205.212 255.255.255.252 0x00001002 rmnet1 DOWN 0.0.0.0 0.0.0.0 0x00001002 rmnet2 DOWN 0.0.0.0 0.0.0.0 0x00001002 sit0 Down 0.0.0.0 0.0.0.0 0x00000080 ip6tnl0 DOWN 0.0.0.0 0.0.0.0 0x00000080 eth0 UP 192.168.25.four 255.255.255.0 0x00001043 Run across the 192.168.25.iv? That could merely as hands be 10.0.0.4, 172.18.34.iv, or any other RFC 1918 address. On many networks (particularly universities) it could even be a public address. T-Mobile has no way of predicting or decision-making what happens on that interface. The 25.0.0.0/8 netblock has the post-obit advantages:
- It doesn't overlap with any other network, public or private. Therefore you lot won't get any routing confusion when the telephone is connected on GPRS/EDGE and WiFi at the same fourth dimension.
- It'southward non in public use. The next Facebook or Lolcats isn't going to show up with a 25.x.x.x address, thereby causing routing defoliation for your users.
- Even if the United kingdom Modernistic is handing out 25.x.x.x address over 802.xi they're way over in the UK. It'southward unlikely that my phone volition exist connected to the MoD and T-Mobile networks at the same fourth dimension.
Why this is insane
IPv4 addresses are getting scarce. Who says the Modernistic won't turn the 25.0.0.0/eight netblock over to RIPE or IANA side by side week? Even then my phone has to go through a proxy server on T-Mobile's network then information technology'southward probably non a huge bargain.
Update
Merely earlier publishing this I ran netcfg and my phone was using 14.64.186.160. The fourteen.0.0.0/8 netblock used to be reserved for public data networks simply was allocated to APNIC earlier this calendar month. I wonder what other questionable netblocks they're using.
A couple of weeks ago nosotros had a foreign problem in the CACE Technologies World Domination Secret Lair. Loris was having trouble loading the Wireshark blog. It was working fine on my machine and then I checked some of the other machines in the role. I found the same trouble on one of the development machines. Loading the page in Firebug showed that the object requests were stalling out every twenty seconds or so:
I fired upwardly Wireshark and captured the browser attempting to connect to the blog:
The trouble was immediately obvious. The browser attempted to connect to the blog'southward IPv6 accost (2607:f0d0:2001:e:1::ane), timed out, and connected to the blog's IPv4 address (67.228.110.126).
As it turns out Loris and I ran some IPv6 tests a long time ago and we added unique local addresses to our machines (mine was fd00:cace::4) . Since each motorcar had an IPv6 accost the TCP stack assumed that at that place was general IPv6 connectivity. However, our ISP is steadfastly ignoring IPv6 and so finish-to-end connectivity wasn't in that location. After timing out the connection barbarous back to IPv4 and proceeded unremarkably.
This sort of thing will probable crop up more and more oft as nosotros transition to IPv6. If either IPv4 or IPv6 connectivity fails, your applications will all the same have connectivity so the failure may not be immediately obvious. In this case Firefox stalled out but even so managed to connect. If it used a connect-by-name socket API the failure wouldn't accept been evident at all.
Today I followed the announcement of the new Chrome OS from Google and the acclaiming response information technology received. Am I the only one thinking: very uncomplicated, maybe TOO simple?
Since the beginning of the "browser as an Bone" idea, I always wondered how I am supposed to run my favorite program, Wireshark, in a browser. Wireshark, of grade, is an example, just many people practise things with computers that don't translate well into the cloud prototype. Will they just be dismissed by OS manufacturers as a "nerdy minority"? Or will they need to stick with old uncool OSes to do their things? I'd similar to be cool also, Google, but I'd still similar to run Wireshark.
Another thing I feel weird about: Google is telling me not to worry about data loss, because from now on all my documents volition exist online. Zero volition need to exist saved locally.
Actually, I like that my documents stay in my computer. Am I really the but one in the world? I'm non only talking about personal stuff like the love letters to my wife or the drunk pictures at the political party terminal week. What nigh the trace files that I go all the fourth dimension from customers? Will they take to go online too? Hmm, I'm sure my customers will love having them on Google'due south server.
I can already hear the objection: "this OS is for netbooks, and netbooks are simply used for unproblematic things like going online, so this is perfect for them". Actually, I love using Wireshark on a netbook! Together with an Airpcap adapter, it'due south the perfect portable wireless troubleshooting station.
Why does small need to mean "limited"? Personally, I'd actually dear to run Wireshark on my wireless-enabled IPod Affect! Ok, peradventure I'm going too far…
http://googleblog.blogspot.com/2009/07/introducing-google-chrome-os.html
We utilise Polycom SoundPoint IP phones here at the CACE Technologies World Domination Secret Lair. While troubleshooting a different problem recently I noticed that the phones do something funny. During the boot procedure they obtain an IP accost via DHCP, similar to most PCs. A DHCP option tells the phones to fetch their configuration and firmware from an FTP server. The funny part is that some of the FTP transfers were failing fifty-fifty though the phones booted up but fine:
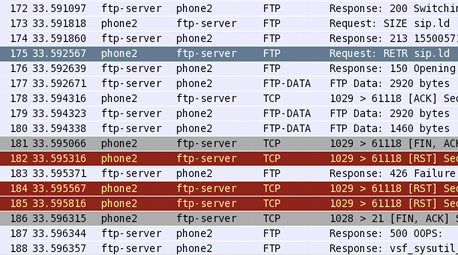
SIP firmware download failure
At parcel 175 the phone starts to download sip.ld, the SIP firmware image. The transfer starts at packet 177, but the telephone cuts the transfer brusk at packet 181. The phone and so behaves as if nothing is wrong. What's going on here? Continue reading
Source: https://blog.wireshark.org/category/analysis/
Posted by: pontonthereaming.blogspot.com


0 Response to ""25.x.x.x" Registered To The Uk Ministry Of Defense?"
Post a Comment